There is a huge amount of protection for the operating system and the computer as a whole. Some of them represent categories where active protection is implemented (antiviruses and firewalls), cleaning utilities, preventive protection utilities and much more. All of them offer a certain functionality, which is aimed at the safety of personal data and the integrity of the operating system. This article focuses on a slightly different software called “Shadow Defender”, designed to preserve the confidentiality of data and prevent changes that could lead to the inoperability of the Windows operating system. And the fact that this program can, how to configure and use it, and will be discussed further.

Work with the program Shadow Defender.
Functional
So, “Shadow Defender” is a project of the company of the same name, which was released back in 2007, and since then has acquired a fairly solid user base, appreciated the quality and offered functionality. It should be understood that, unlike most other representatives of the anti-virus protection category, Shadow Defender (or “Shadow Protection” in translation) does not attempt to protect information from third-party interference from virus software, but only tries to minimize the risk of damage to this data. This is a key point that must be taken into account in order to avoid possible misunderstandings.
The functionality offered by developers has rather simple and clear basis. The user, at his discretion, determines which categories of files should be further protected. The security system in question begins to create dynamic copies of all selected objects. These copies are called "shadow", because in fact they are only an image that reflects the general state and content of the file. The safety of the copy is achieved through the use of a virtual environment (Shadow Mode), where all the elements are placed, without any impact on the other "environment". In fact, all selected objects are simply fixed (or “frozen”) in a certain state, which will be reset (if desired) after a reboot. This state does not allow viruses to consolidate in the “frozen sectors”, which ensures such a high level of protection.
In this approach, there is a significant flaw that has already been indicated earlier - this is a possible loss of information if the virus managed to gain a foothold in the “environment”, compromise all the data it needs and retire after rebooting the system. The fact of infection may remain unidentified, since the virus is no longer there, but the data have already lost their “secrecy”. “Shadow Defender” is an ideal tool that should be used as an additional anti-virus barrier with specialized software.
How to install and configure
"Shadow Defender" is distributed on a paid license worth $ 25, but it also has a 30-day trial version, which will demonstrate that for such security the amount is not that great. In order to download the utility, you should visit the official website of the developers - //www.shadowdefender.com, where you can also download the file from the Russian localization, as the default interface is in English. After downloading the executable file and installing the software, place the resulting localization file (res.ini) in the root folder “Shadow Defender”, after changing the extension of the previous file.

Run the program and select the option you need (purchase a license or stay on the temporary demo version), after which the main interface of the program will become available, which consists of six main sections, namely:
- “System status” - in this tab you can get acquainted with the basic information about the state of disk partitions, that is, how much free space remains, as well as how much the program itself takes.
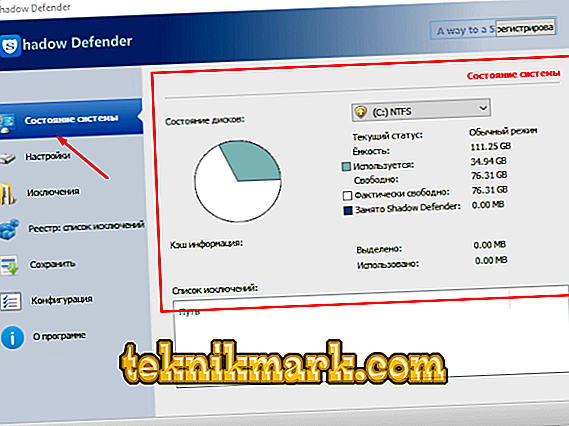
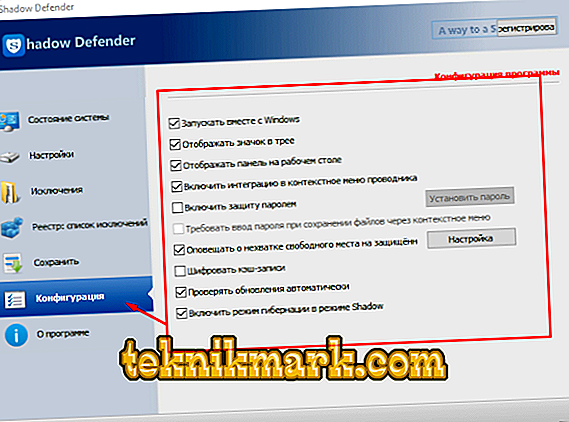
- “Settings” is the main section where the user activates the “shadow protection”. To initiate, it is enough to mark the necessary disks with checkboxes and click on the “Protected mode” button. If the amount of RAM is sufficient, then you can additionally allocate a part of it for cache storage.
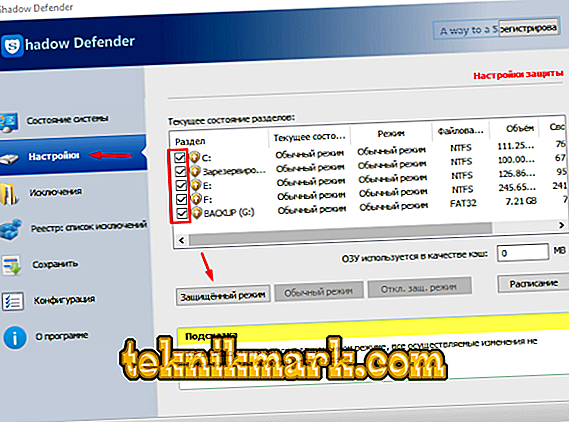
By clicking on the "Schedule" button, you can choose whether to disable protected mode when you turn off the computer or leave it to work after a reboot. The same sentence will be displayed after clicking on the “Protected mode” button.
- “Exceptions” - the more objects placed under the “shadow protection”, the more the program requires free memory.
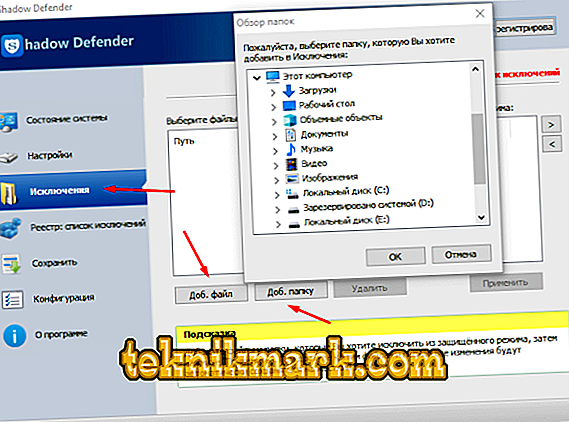
In addition, there are files that do not require additional charm, so it would be better to include them in the list of exceptions in order to free up resources for safeguarding the really important / personal / confidential data.
- “Registry: list of exceptions” - the above statement applies (albeit to a lesser extent) to the protection of registry values / keys.
- “Save” - allows you to select objects, changes of which will be saved to the hard disk resources.
- "Configuration" - offers several customizable parameters to ensure maximum effect from the use of all functionality. For example, you can set a password to enable / disable shadow mode, set up alerts that will notify you when a hard disk is running out, where program files are stored, etc.
How to check and remove the program
In order to check the quality of the utility, it is enough to do the following:
- On the selected disk partition, create a folder with any name and carry out any actions with it (delete, rename, change location).
- Open the utility interface and deactivate the shadow mode.
- If the test folder was on the system partition, then a window will open in front of you that it is currently impossible to perform this action and a reboot is required.
- After the reboot, the deleted folder “magically” will appear in the same place.
This will spread to the entire section as a whole, even the browser history and open tabs will return to the time period when “Shadow Mode” was disabled. Really worthwhile functionality, for which it is not a pity to part with $ 35. But if for some reason you were not interested in the possibilities of the software in question, you can remove the program using the standard tools of the operating system in the "Programs and Features" section.
Conclusion
Tools to ensure the safety of the operating system should be treated with a certain degree of distrust and not rely on them entirely. Whatever advanced the antivirus system is, there can always be a loophole, and “Shadow Defender” is no exception. A well-considered approach to the use of existing tools is the key to preserving the integrity of Windows and the entire contents of a computer.







